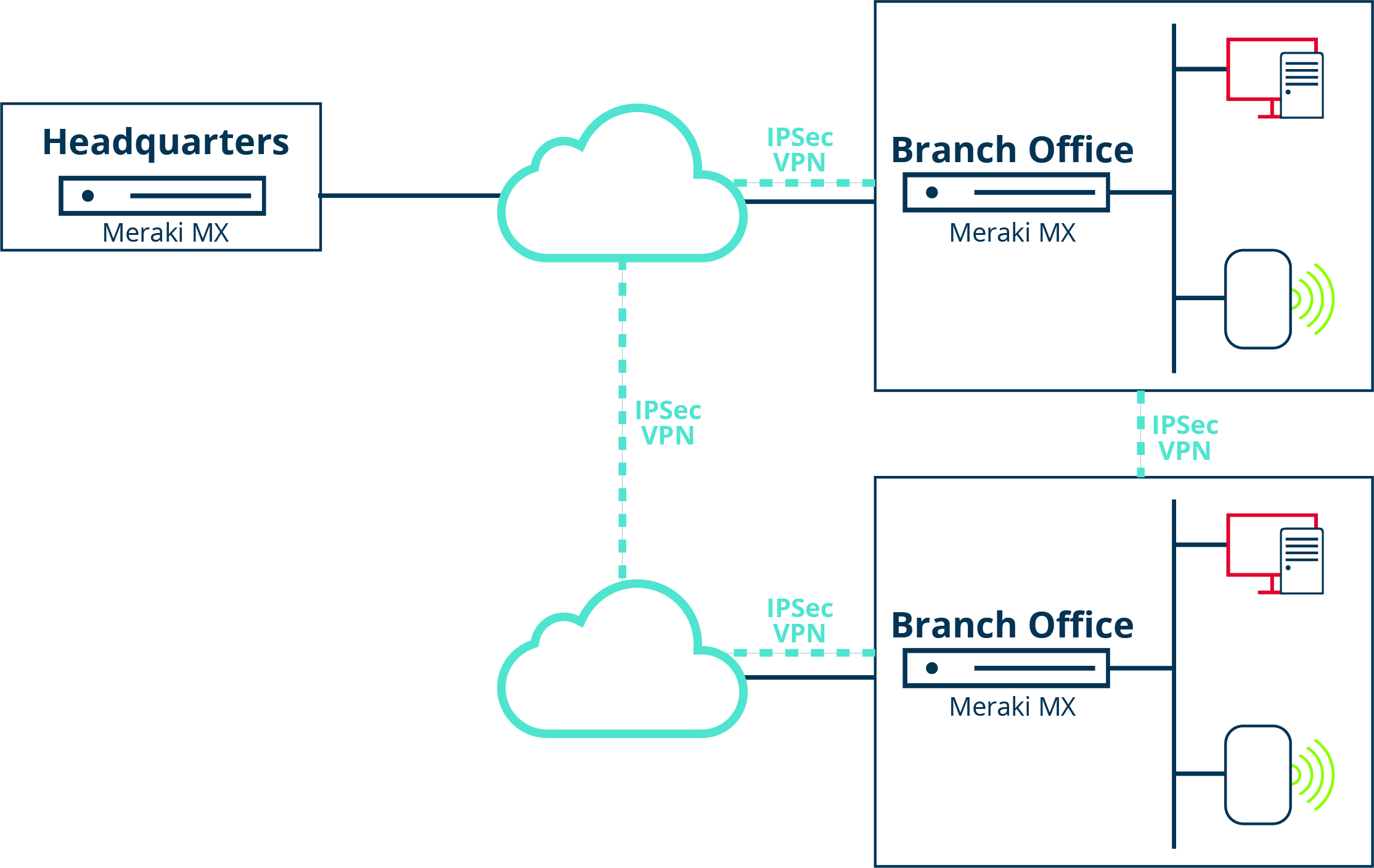
The MX appliances elegantly create a framework for Cisco SD-WAN powered by Meraki by securely auto-provisioning IPsec VPN tunnels between sites. The Meraki dashboard automatically negotiates VPN routes, authentication and encryption protocols, and key exchange for all Meraki MX appliances in an organization to create hub-and-spoke or mesh VPN. Azure marketplace and then configured in the Meraki dashboard, just like any other MX. It functions like a VPN concentrator and features SD-WAN functionality like other MX devices. An Auto VPN to a virtual MX is like having a direct Ethernet connection to a private data center. The virtual MX can support up to.
Syslog Configuration
A syslog server can be configured to store messages for reporting purposes from MX security appliances, MR access points, and MS switches. The MX Security Appliance supports sending four categories of messages/roles: Event Log, IDS Alerts, URLs, and Flows. MR access points can send the same roles with the exception of IDS alerts. MS switches currently only support Event Log messages.
To begin setting up a Syslog server on the Meraki dashboard, first, navigate to Network-Wide > Configure > General. Here you will see a section for Reporting, with the option for Syslog server configurations. Click on the Add a syslog server link to define a new server. Configure an IP address of your syslog server, the UDP port the server is listening on, and the roles you wish to be reported to the server.
If the Flows role is enabled for Meraki MX reporting, logging for individual firewall rules can be enabled/disabled on the Security appliance > Configure > Firewall page, under the Logging column as shown below:
Additional Considerations for Syslog
Storage Allocation
Cisco Ssl Vpn Download
Syslog messages can take up a large amount of disk space, especially when collecting flows. When deciding on a host to run the syslog server, make sure to have enough storage space on the host to hold the logs. Consult the syslog-ng man page for further information on only keeping logs for a certain amount of time.
Expected Traffic Flow
Syslog traffic may flow to the syslog in one of three scenarios depending on the route type that is used to reach the syslog server. Below are example scenarios and a detailing of expected traffic behavior.
Scenario 1 - Reachable via LAN

The MX will source traffic from the VLAN interface that the server resides in if the syslog server is located on the LAN of the MX. The transit VLAN interface would be used if the device is only accessible via static route. Autocad architecture.
Scenario 2 - Reachable via Public Interface
The MX will source traffic from the public interface (WAN) if the syslog server is accessible via the WAN link.
Scenario 3 - Reachable via AutoVPN

The MX will source traffic from the interface of the highest VLAN that is participating in AutoVPN if the syslog server is accessible via AutoVPN.
Ssl Vpn Client
If the traffic passes through the site-to-site AutoVPN connection the traffic will then be subject to the 'Site-to-site outbound firewall' rules and as such an allow rule may be required. This can be configured in Security appliance > Configure > Site-to-site VPN > Organization-wide settings > Add a rule as shown below.
